FALCO

WHAT IS FALCO?
The Falco Project is an open source runtime security tool originally built by Sysdig, Inc. Falco was donated to the CNCF and is now a CNCF incubating project.
Falco makes it easy to consume kernel events, and enrich those events with information from Kubernetes and the rest of the cloud native stack. Falco has a rich set of security rules specifically built for Kubernetes, Linux, and cloud-native. If a rule is violated in a system, Falco will send an alert notifying the user of the violation and its severity. Falco started life as an open source behavioral activity monitoring agent. Described as a mix between snort, ossec, and strace, Rather than using a signature-based security monitoring approach, which looks for specific exploits and vulnerabilities, Falco looks for suspicious system activities, which show an attacker may be at work.

WHAT DOES FALCO DO?
Falco uses system calls to secure and monitor a system, by:
- Parsing the Linux system calls from the kernel at runtime
- Asserting the stream against a powerful rules engine
- Alerting when a rule is violated
WHAT DOES FALCO CHECK FOR?
Falco ships with a default set of rules that check the kernel for unusual behavior such as:
- Privilege escalation using privileged containers
- Namespace changes using tools like setns
- Read/Writes to well-known directories such as /etc, /usr/bin, /usr/sbin, etc
- Creating symlinks
- Ownership and Mode changes
- Unexpected network connections or socket mutations
- Spawned processes using execve
- Executing shell binaries such as
sh,bash,csh,zsh, etc - Executing SSH binaries such as
ssh,scp,sftp, etc - Mutating Linux coreutils executables
- Mutating login binaries
- A shell is running inside a container or pod in Kubernetes.
- A container is running in privileged mode, or is mounting a sensitive path, such as
/proc, from the host. - A server process is spawning a child process of an unexpected type.
- Unexpected read of a sensitive file, such as
/etc/shadow. - A non-device file is written to
/dev. - A standard system binary, such as
ls, is making an outbound network connection. - A privileged pod is started in a Kubernetes cluster.
- Mutating shadowutil or passwd executables such as shadowconfig, pwck, chpasswd, getpasswd, change, useradd, etc, and others.
WHY FALCO?
Signature-based approaches are engaged in a never-ending game of catch up with the constant stream of new threats. Behavioral monitoring based approaches, in contrast, look at what is happening on a system and can immediately alert if something malicious occurs.
With Falco, you can create detection rules to define unexpected application behavior. These rules can be enriched via context from the Kubernetes environments. Your teams can detect policy violations using community-sourced detections of malicious activity and CVE exploits. They can then alert by plugging Falco into your current security response workflows and processes.
BENEFITS OF USING FALCO
- Strengthen container security:
- The flexible rules engine allows you to describe any type of host or container behavior or activity.
- Reduce risk via immediate alerts:
- You can immediately respond to policy violation alerts and integrate Falco within your response workflows.
- Leverage most current detection rules:
- Falco out-of-the box rules alert on malicious activity and CVE exploits.
FALCO ARCHITECTURE
Falco can detect and alert on any behavior that involves making Linux system calls. Falco alerts are triggered based on specific system calls, arguments, and propertiesof the calling process. Falco operates at the user space and kernel space. The system calls are interpreted by the Falco kernel module. The syscalls are then analyzed using the libraries in the userspace. The events are then filtered using a rules engine where the Falco rules are configured. Suspicious events are then alerted to outputs that are configured as Syslog, files, Standard Output, and others.
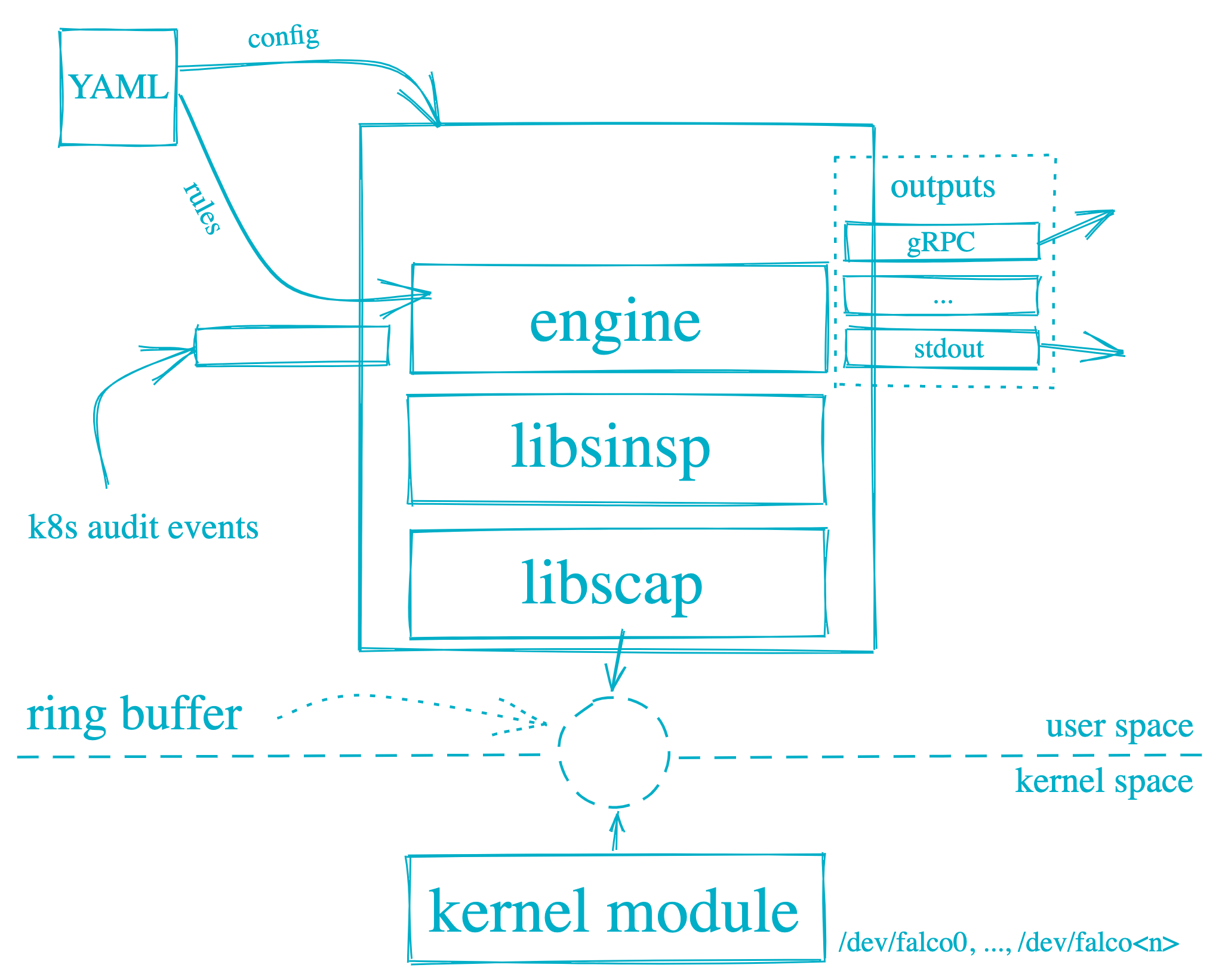 ## COMPONENTS OF FALCO Falco is composed of three main components:
## COMPONENTS OF FALCO Falco is composed of three main components:Userspace program: - is the CLI tool falco that you can use to interact with Falco. The userspace program handles signals, parses information from a Falco driver, and sends alerts.
Configuration: - defines how Falco is run, what rules to assert, and how to perform alerts. For more information, see Configuration.
Driver: - is a software that adheres to the Falco driver specification and sends a stream of system call information. You cannot run Falco without installing a driver. Currently, Falco supports the following drivers:
- (Default) Kernel module built on libscap and libsinsp C++ libraries
- BPF probe built from the same modules
- Userspace instrumentation
CONFIGURATION
Falco's configuration file is a YAML file containing a collection of key: value or key: [value list] pairs.
Any configuration option can be overridden on the command line via the -o/--option key=value flag. For key: [value list] options, you can specify individual list items using --option key.subkey=value.
DEVELOPING
Falco is designed to be extensible such that it can be built into cloud-native applications and infrastructure.
Falco has a gRPC endpoint and an API defined in protobuf. The Falco Project supports various SDKs for this endpoint.
FEATURED VIDEOS
To learn more about FALCO watch these videos:
| LINKS |
|---|
| Video 1. |
| Video 2. |
| Video 3. |